
Ethical Hacking & Cyber Security in Ahmedabad
Dive into the exciting world of Cybersecurity and Ethical Hacking with Grras Ahmedabad’s comprehensive course! Perfect for beginners, this program equips you with the essential skills to protect digital systems from cyber threats.

150k+ Placemenets to Date

600+ Hiring Partners

76 Lakhs Highest Annual

Next Batch starts in December






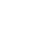



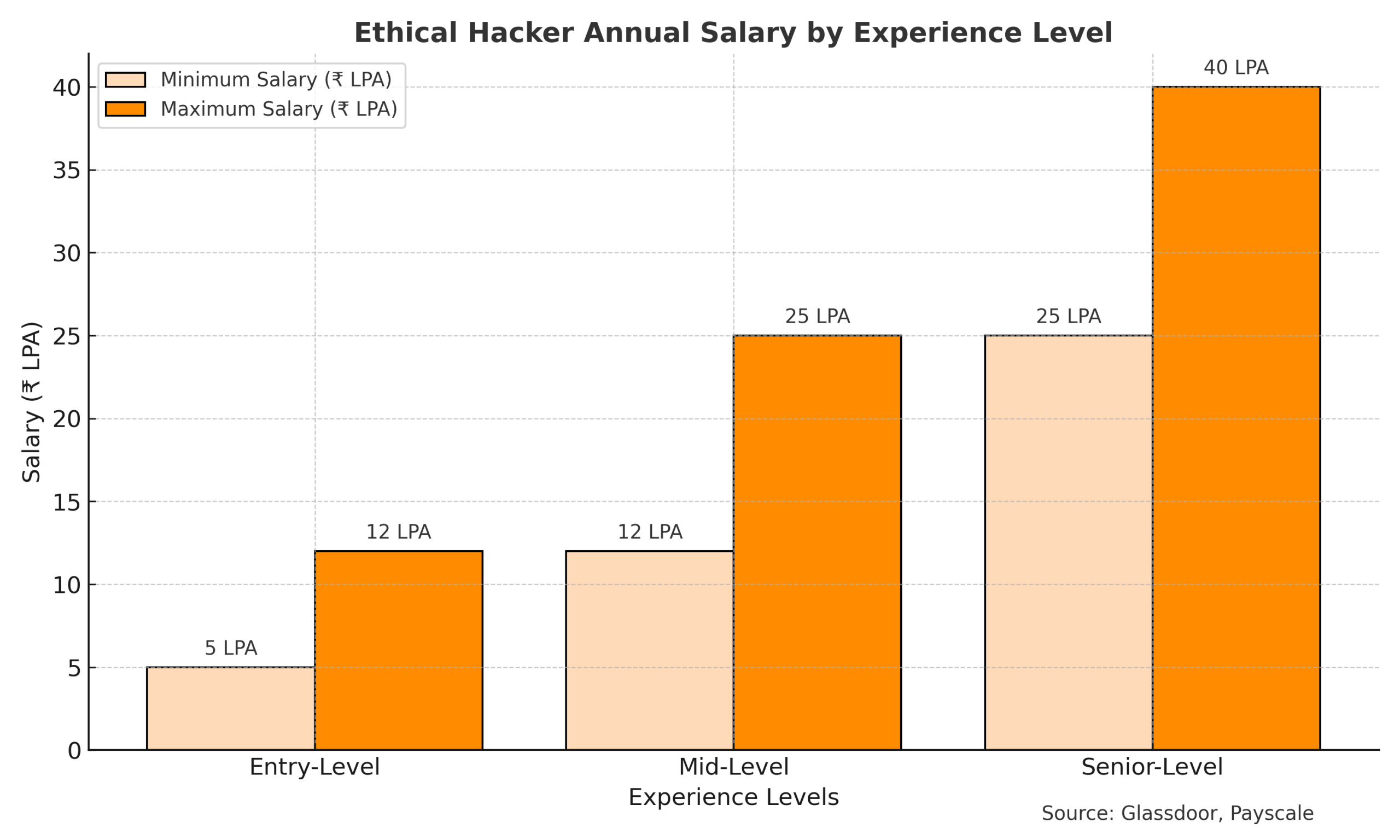

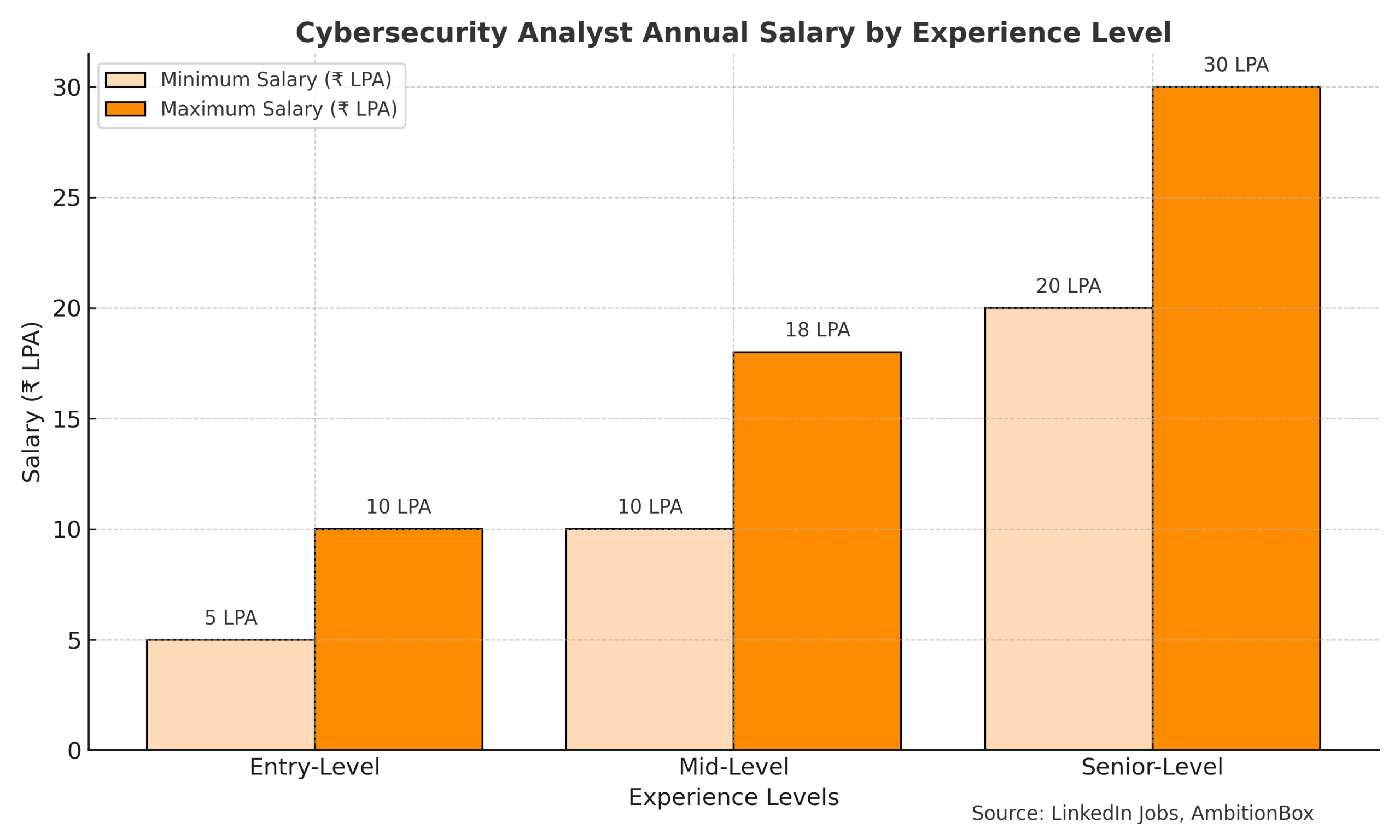

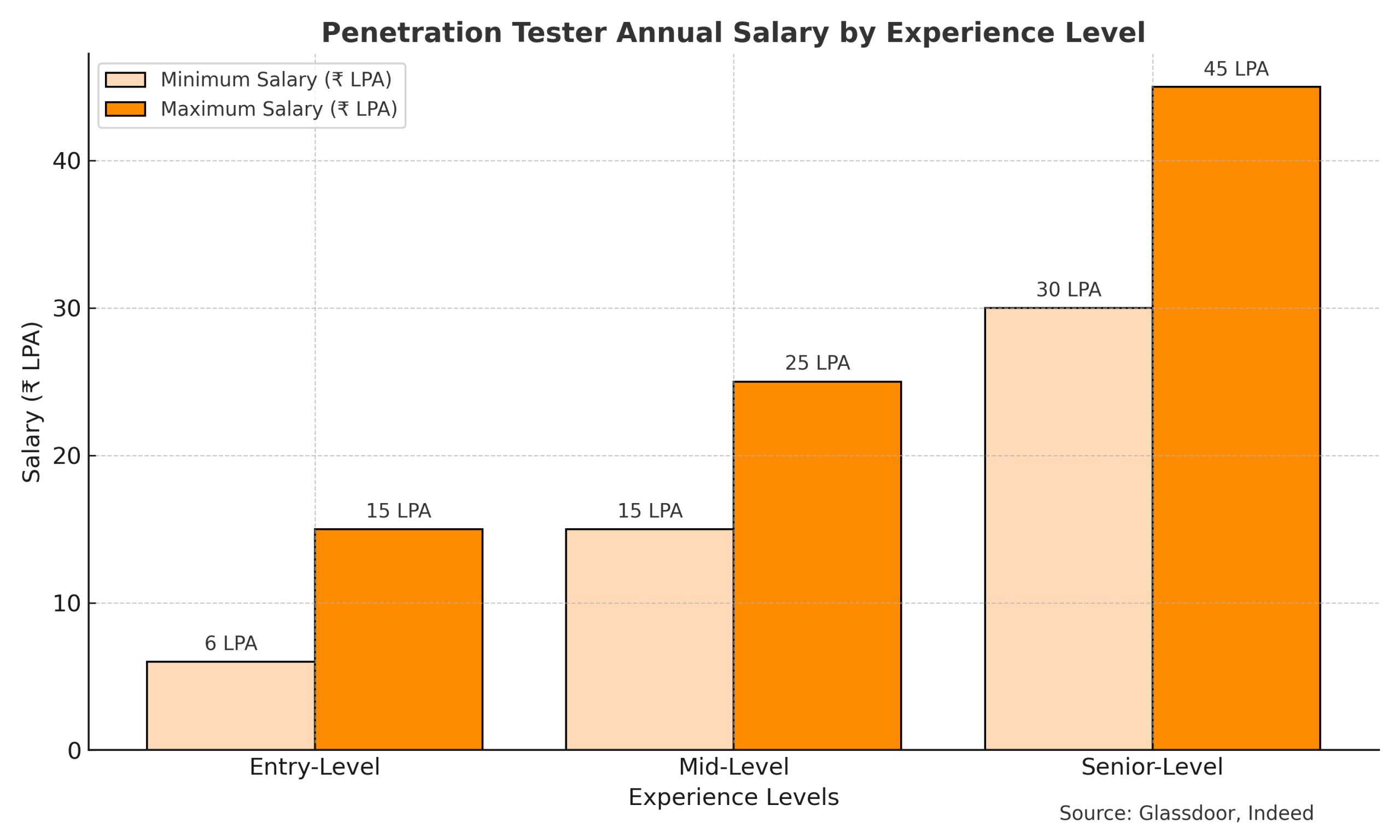

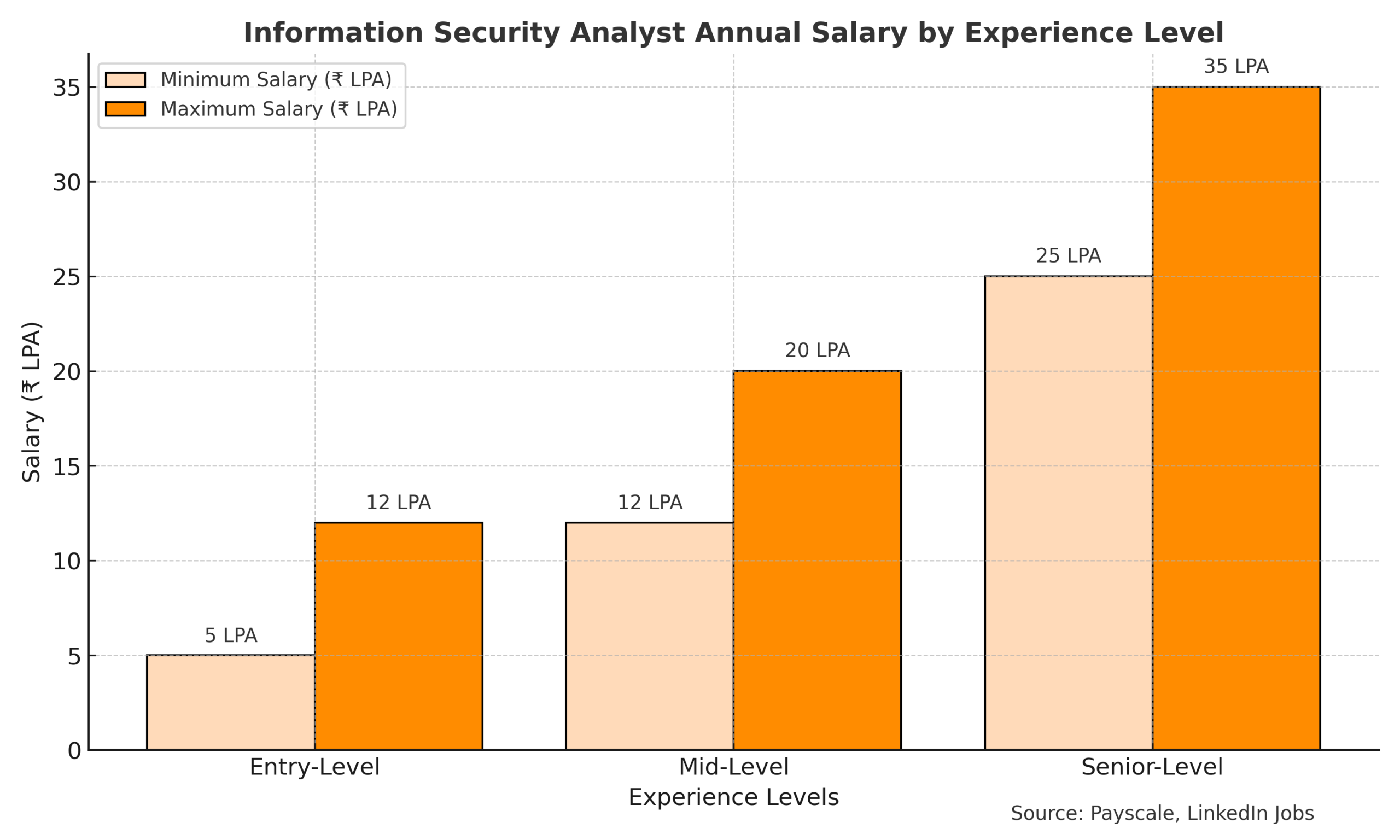

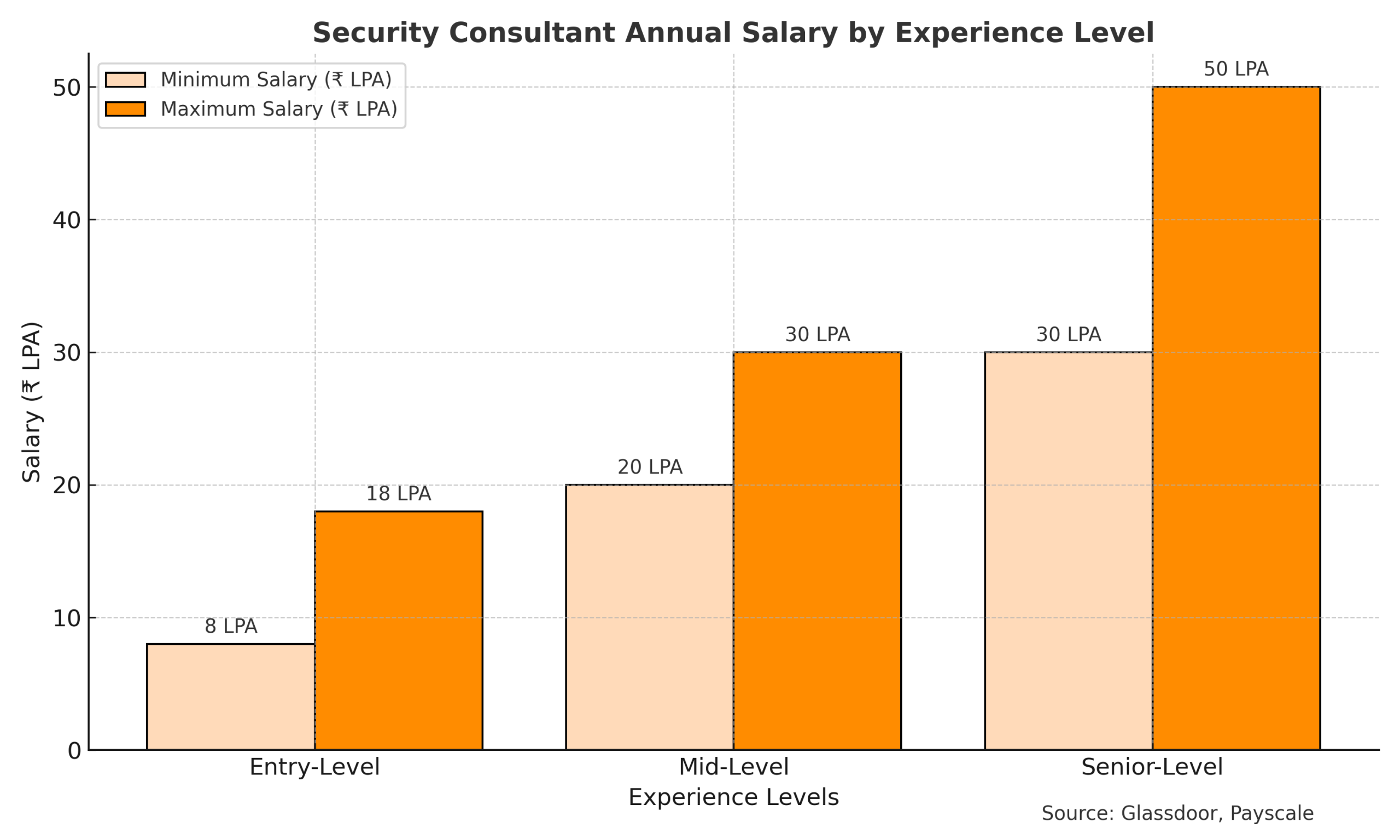

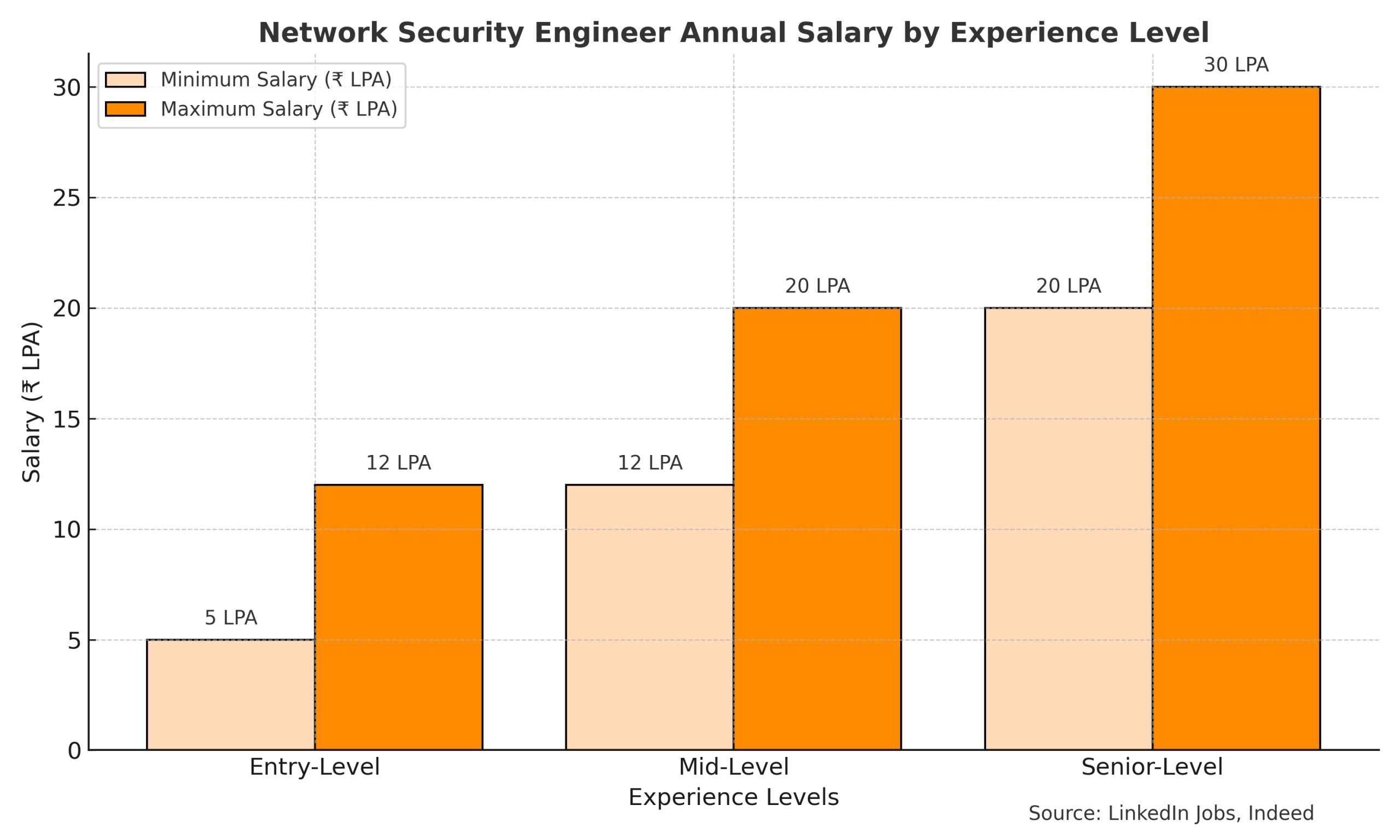

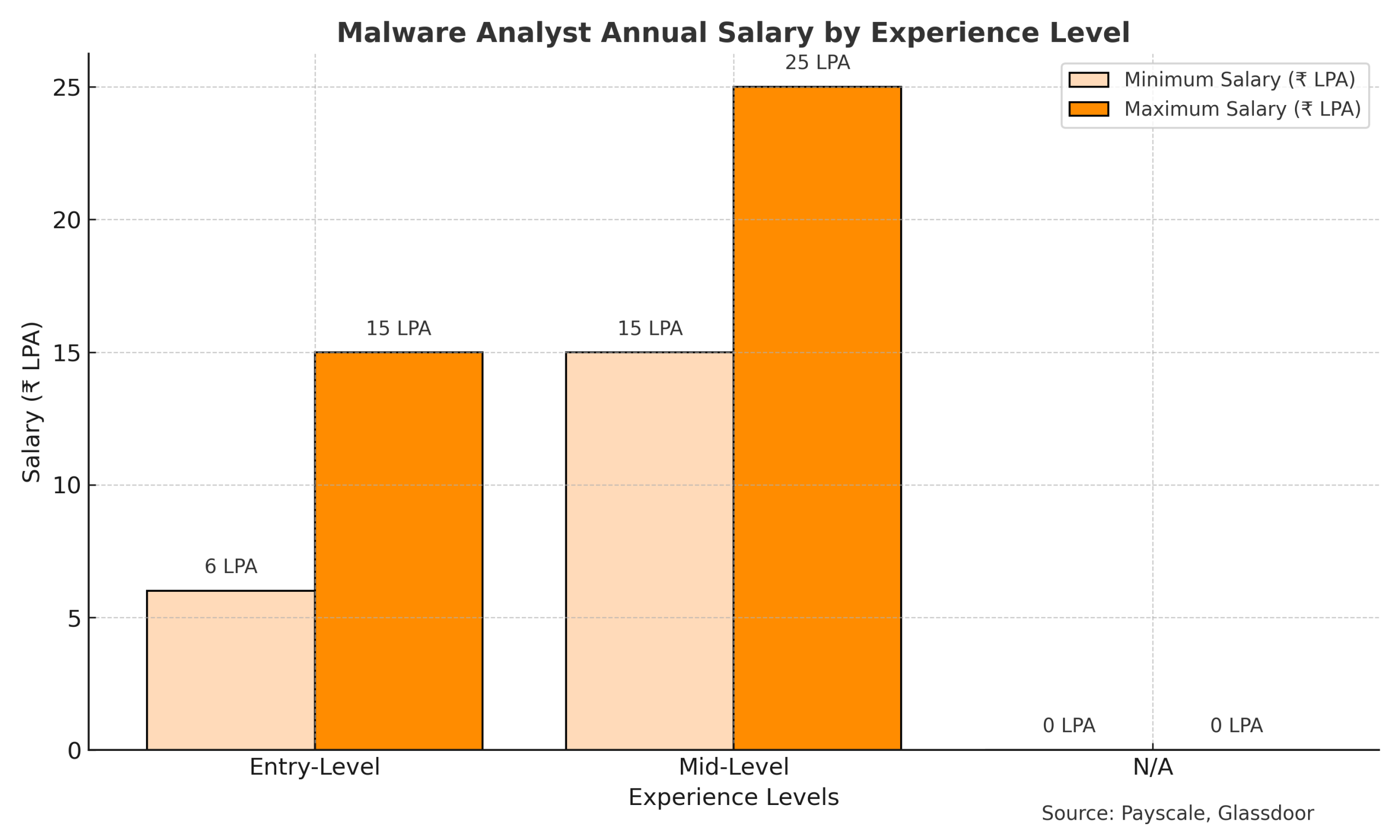
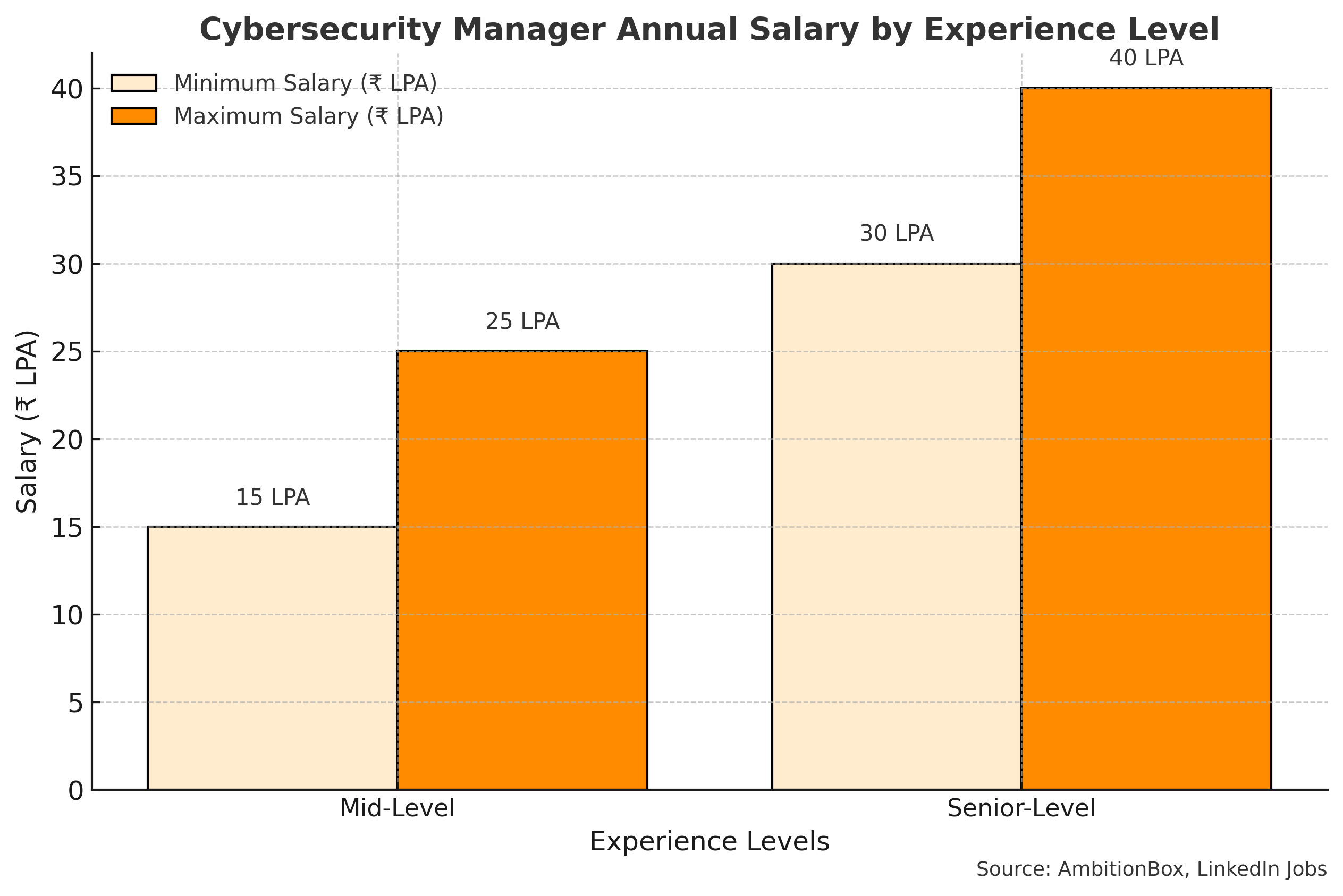
 Duration: 75–80 hours of total training
Duration: 75–80 hours of total training












































 Whatsapp us
Whatsapp us Call us
Call us





